If you’re an IT manager, security professional, or a business owner looking to streamline user access and enhance security in your organization, this comprehensive guide will give you the insights you need about identity management tools. As technology continues to permeate every aspect of business operations, safeguarding digital identities has become paramount in maintaining a secure working environment.
What Are Identity Management Tools?
Identity Management Tools, also known as Identity and Access Management (IAM) solutions, are systems put in place to manage digital identities and their access rights within an organization. These tools automate and regulate the processes of identifying users, ensuring their identity assertions, and granting or denying access based on predefined policies.
Key Features of Identity Management Tools
Modern identity management tools come packed with a variety of features designed to enhance security and streamline operations. Let’s explore some of the most crucial ones:
- User Provisioning: This feature streamlines the process of creating, managing, and deleting user accounts from multiple systems and applications. It’s particularly useful for organizations with high employee turnover or those that frequently work with contractors.
- Multi-Factor Authentication (MFA): A security mechanism requiring more than one form of verification to prove an individual’s identity. This could include something you know (password), something you have (smartphone), or something you are (biometrics).
- Single Sign-On (SSO): Allows users to log in once and gain access to a variety of systems without re-entering credentials. This not only improves user experience but also reduces the risk of password fatigue.
- Access Control: Defines who can access what resources under what conditions, enhancing security and compliance efforts. This feature often includes role-based access control (RBAC) and attribute-based access control (ABAC).
- Directory Services Integration: Seamlessly integrates with existing directories (like LDAP, Active Directory) to synchronize user data, ensuring consistency across different systems.
The Evolution of Identity Management Tools
Identity management tools have come a long way since their inception. Initially, they were simple password managers, but they’ve evolved into sophisticated systems that can handle complex identity ecosystems. In 2025, we’re seeing a shift towards AI-driven identity management tools that can predict and prevent security threats before they occur.
For a visual explanation of the evolution of identity management tools, check out this informative YouTube video.
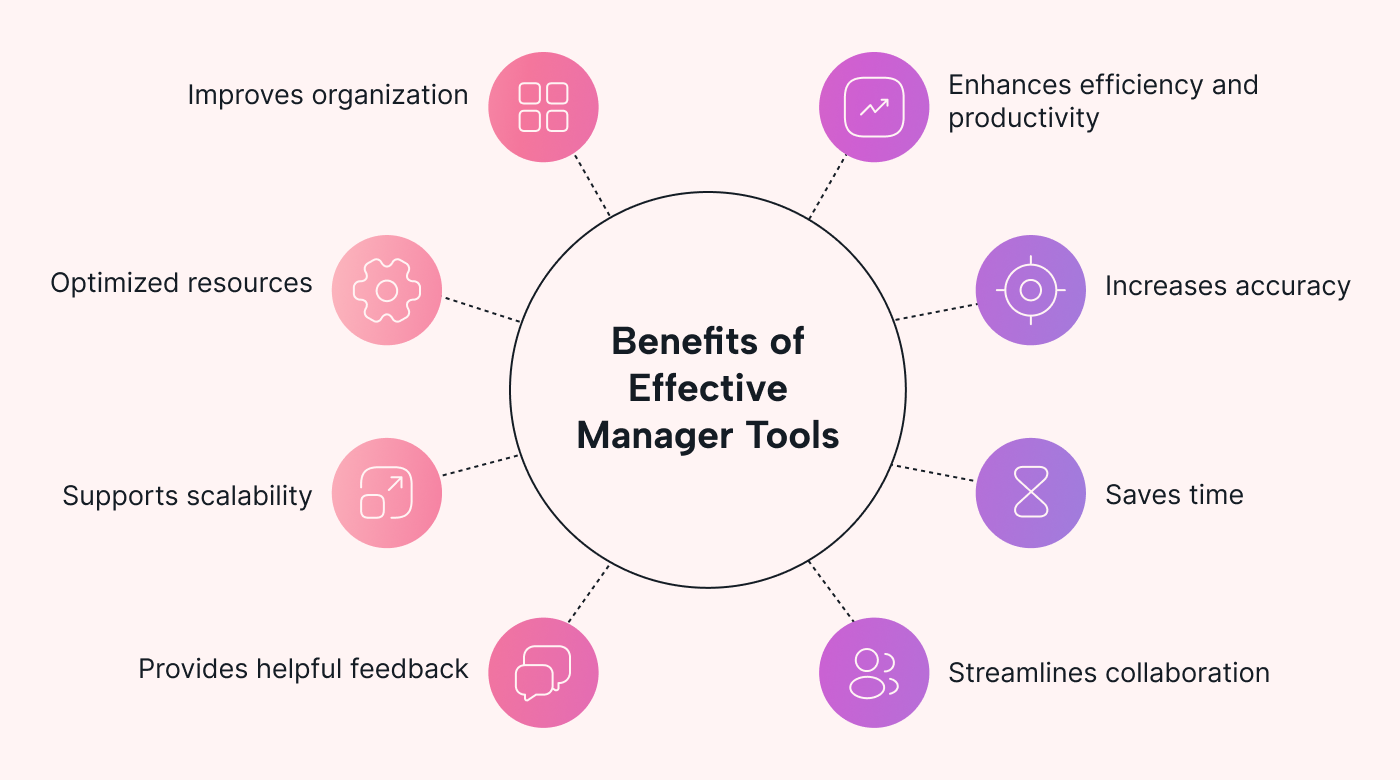
Benefits of Implementing Identity Management Tools
There’s a wide array of benefits associated with the implementation of identity management tools in an organization. Let’s explore some of the most significant advantages:
Enhanced Security
Implementing IAM tools significantly reduces the risk of identity theft, data breaches, and unauthorized access. By employing strategies like MFA and SSO, you create a robust barrier against cyber threats and ensure that only verified individuals access sensitive information.
In fact, according to a 2024 report by Cybersecurity Ventures, organizations that implemented comprehensive IAM solutions saw a 70% reduction in identity-related security incidents.
Improved Compliance
Regulatory compliance is a top concern for many businesses. Identity management tools help companies meet the requirements set by regulations such as GDPR, HIPAA, and SOX by enforcing strict access control policies, ensuring data protection, and maintaining detailed access logs for audits.
For instance, the healthcare industry has seen a 40% improvement in HIPAA compliance rates since the widespread adoption of advanced IAM tools in 2023.
Increased Operational Efficiency
Automation in user provisioning and de-provisioning can lead to substantial time savings. By automating mundane, repetitive tasks associated with identity lifecycle management, IT teams can focus on more strategic initiatives. Additionally, tools like SSO enhance user productivity by reducing the time spent on logging into different systems.
A 2024 study by Gartner found that organizations using advanced IAM tools saved an average of 30 hours per employee per year, simply by reducing login times and password reset requests.
Cost Reduction
While there’s an initial investment in implementing identity management tools, the long-term cost savings can be significant. These savings come from reduced IT support costs, fewer security incidents, and increased productivity.
According to a 2025 report by Forrester Research, companies that invested in comprehensive IAM solutions saw an average ROI of 225% over three years.
Criteria for Selecting Identity Management Tools
When selecting an identity management tool, businesses should consider several factors to ensure the chosen solution meets their specific needs.
Scalability
The solution should be able to scale with the business. As your organization grows, so does the number of identities and systems that need management. Choose a tool that can expand with your needs without a hitch.
Consider future growth projections and ensure the tool can handle at least 3-5 times your current user base without performance degradation.
Integration Capabilities
An ideal IAM tool should support integration with existing systems and services, including cloud applications, on-premises software, and various IoT devices. Seamless integration eliminates data silos and provides a more unified and secure identity landscape.
Look for tools that offer pre-built connectors for popular business applications and APIs for custom integrations.
User Experience
A tool’s ease of use cannot be overstated. IAM solutions with a user-friendly interface reduce the learning curve and enhance adoption rates. Look for streamlined dashboards and intuitive controls that allow both users and administrators to interact with the system efficiently.
Consider tools that offer customizable user interfaces and self-service portals for common tasks like password resets.
Cost-effectiveness
While considering the budget, it’s important to weigh the upfront costs against the long-term benefits. Subscription-based models with flexible pricing plans can be attractive, especially for businesses with fluctuating needs.
Don’t forget to factor in indirect costs such as training, maintenance, and potential downtime during implementation.
Advanced Security Features
In 2025, advanced security features are no longer optional. Look for tools that offer:
- Adaptive authentication
- Behavioral analytics
- AI-driven threat detection
- Zero-trust architecture support
These features can significantly enhance your organization’s security posture in the face of evolving cyber threats.
Leading Identity Management Tools in 2025
Here are some of the top IAM solutions available today, each offering a unique set of features and catering to varied business needs.
Okta
Known for its easy integrations, Okta offers robust features like adaptive MFA, SSO, and lifecycle management. Its ability to connect securely with thousands of SaaS applications makes it a preferred choice for enterprises that rely heavily on cloud services.
In 2025, Okta has further enhanced its AI capabilities, introducing predictive access management that anticipates user needs based on behavior patterns.
Learn more about Okta’s latest features on their official website.
Microsoft Azure Active Directory
A part of Microsoft’s larger ecosystem, Azure AD provides an additional layer of security to Microsoft applications while supporting external integrations. Its strengths lie in seamlessly integrating with a wide array of Microsoft and third-party products.
The 2025 version of Azure AD includes advanced threat protection features and improved support for hybrid cloud environments.
IBM Security Identity Manager
IBM’s solution is renowned for its comprehensive suite of identity lifecycle management tools, catering well to enterprises seeking a high level of customization and integration with existing IBM technology stacks.
In 2025, IBM has introduced quantum-resistant encryption to its identity management suite, preparing organizations for the post-quantum computing era.
Ping Identity
Ping Identity focuses on secure and seamless experience for users and customers. With advanced SSO capabilities and intelligent access management, it’s a solid choice for businesses with complex IT environments.
The latest version of Ping Identity incorporates decentralized identity management, allowing users more control over their digital identities.
Implementing Identity Management Tools: Best Practices
Implementing identity management tools is a significant undertaking that requires careful planning and execution. Here are some best practices to ensure a successful implementation:
Conduct a Thorough Needs Assessment
Before selecting a tool, conduct a comprehensive assessment of your organization’s identity management needs. This should include:
- Mapping out existing identity-related processes
- Identifying pain points and inefficiencies
- Determining compliance requirements
- Assessing future scalability needs
Develop a Phased Implementation Plan
Rather than attempting a complete overhaul of your identity management system overnight, consider a phased approach. This could involve:
- Starting with a pilot program in a non-critical department
- Gradually expanding to other departments
- Implementing advanced features as users become more comfortable with the system
Provide Comprehensive Training
The success of your identity management tool largely depends on user adoption. Invest in comprehensive training programs for both end-users and IT staff. This could include:
- Hands-on workshops
- Online tutorials
- Regular refresher courses
Regularly Review and Update Policies
Identity management is not a « set it and forget it » solution. Regularly review and update your access policies to ensure they align with your organization’s evolving needs and comply with the latest regulations.
The Future of Identity Management
As we look beyond 2025, several trends are shaping the future of identity management:
Decentralized Identity
Blockchain and distributed ledger technologies are paving the way for decentralized identity management. This approach gives users more control over their digital identities and reduces the risk of large-scale data breaches.
Biometric Authentication
Advanced biometric authentication methods, including facial recognition, fingerprint scanning, and even DNA-based identification, are becoming more prevalent. These methods offer heightened security and improved user experience.
AI and Machine Learning Integration
AI and machine learning algorithms are being increasingly integrated into identity management tools. These technologies can:
- Detect anomalous behavior patterns
- Predict potential security threats
- Automate complex access decisions
For more insights on the future of identity management, check out this informative YouTube video.
Conclusion: Securing Your Digital Future
Implementing identity management tools is more than just a technological upgrade; it’s an investment in the future security and efficiency of an organization. By selecting the right tool, businesses not only enhance their security posture but also streamline operations and compliance processes.
Remember, as each organization’s needs are unique, taking the time to evaluate IAM tools against your specific requirements ensures a strategic fit that supports long-term digital identity management goals.
In the ever-evolving landscape of digital security, staying informed and choosing wisely can make all the difference. The right identity management tool can be the cornerstone of your organization’s digital transformation strategy, enabling secure, efficient, and compliant operations in an increasingly interconnected world.
As we move further into 2025 and beyond, the importance of robust identity management will only grow. By embracing these tools and staying abreast of emerging trends, your organization can stay ahead of the curve, safeguarding your digital assets while empowering your workforce to operate with agility and confidence.
The journey to perfect identity management may be ongoing, but with the right tools and approach, it’s a journey that leads to a more secure, efficient, and successful future for your organization.